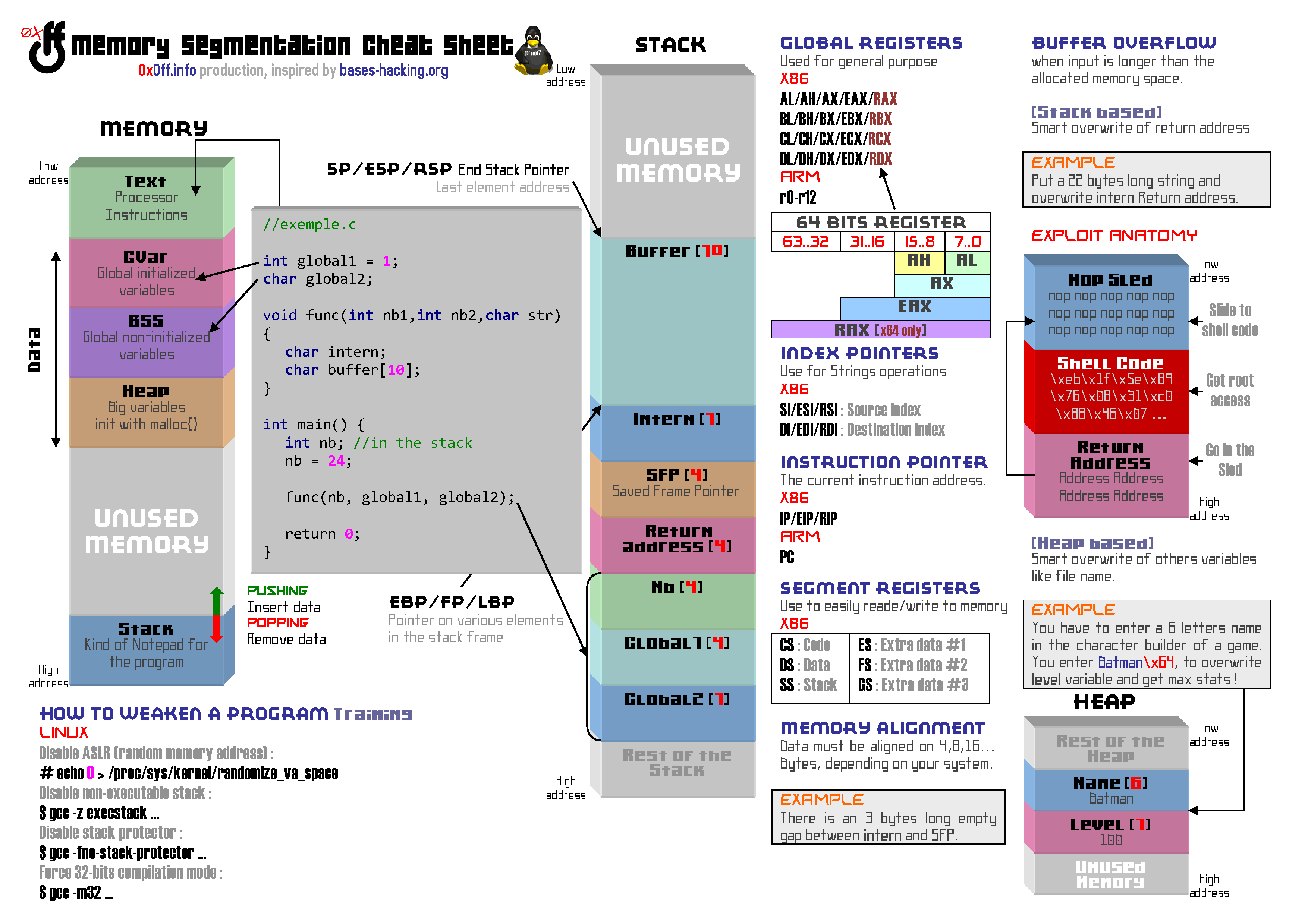
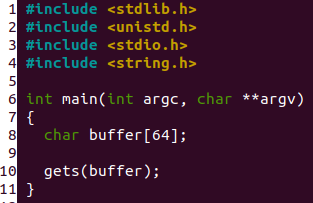
x86 stack protector code references @GOTPCREL and @PLT even when built with -fno-pic or -fno-pie · Issue #62481 · llvm/llvm-project · GitHub

LAB - Chapter 3.2 - Software Security_Buffer_Overflow | PDF | Computer Programming | Software Engineering

C++ code (TSF.c) Compiling this code using the command 'gcc TSF.c -z... | Download Scientific Diagram

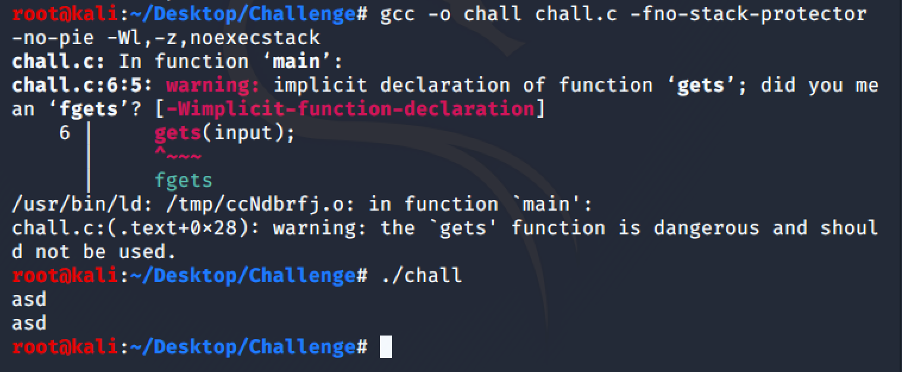
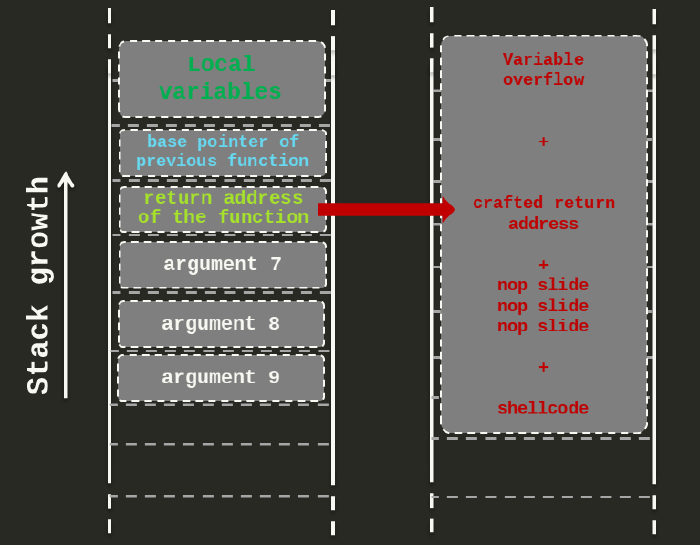
Steps (Linux Ubuntu) - 1) Showing vulnerable code. 2) Compiling program w/o stack protector. 3) Assigning it to root. 4) Enabling it to run as root. 5) Creating…
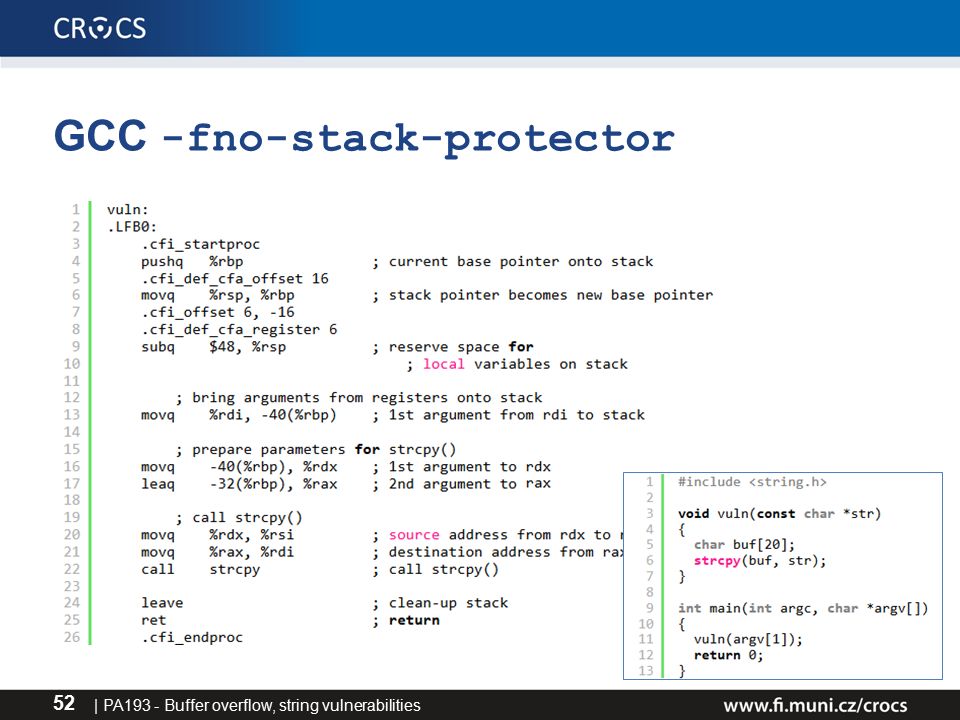
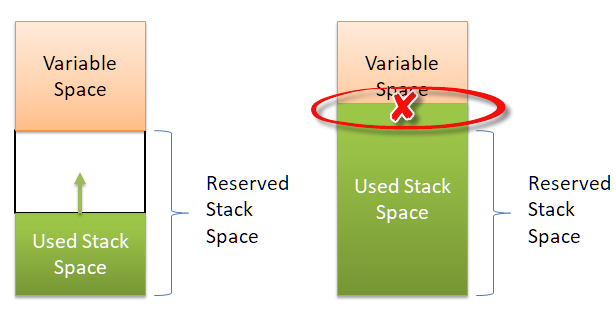
PA193 - Secure coding principles and practices Language level vulnerabilities: Buffer overflow, type overflow, strings Petr Švenda - ppt download
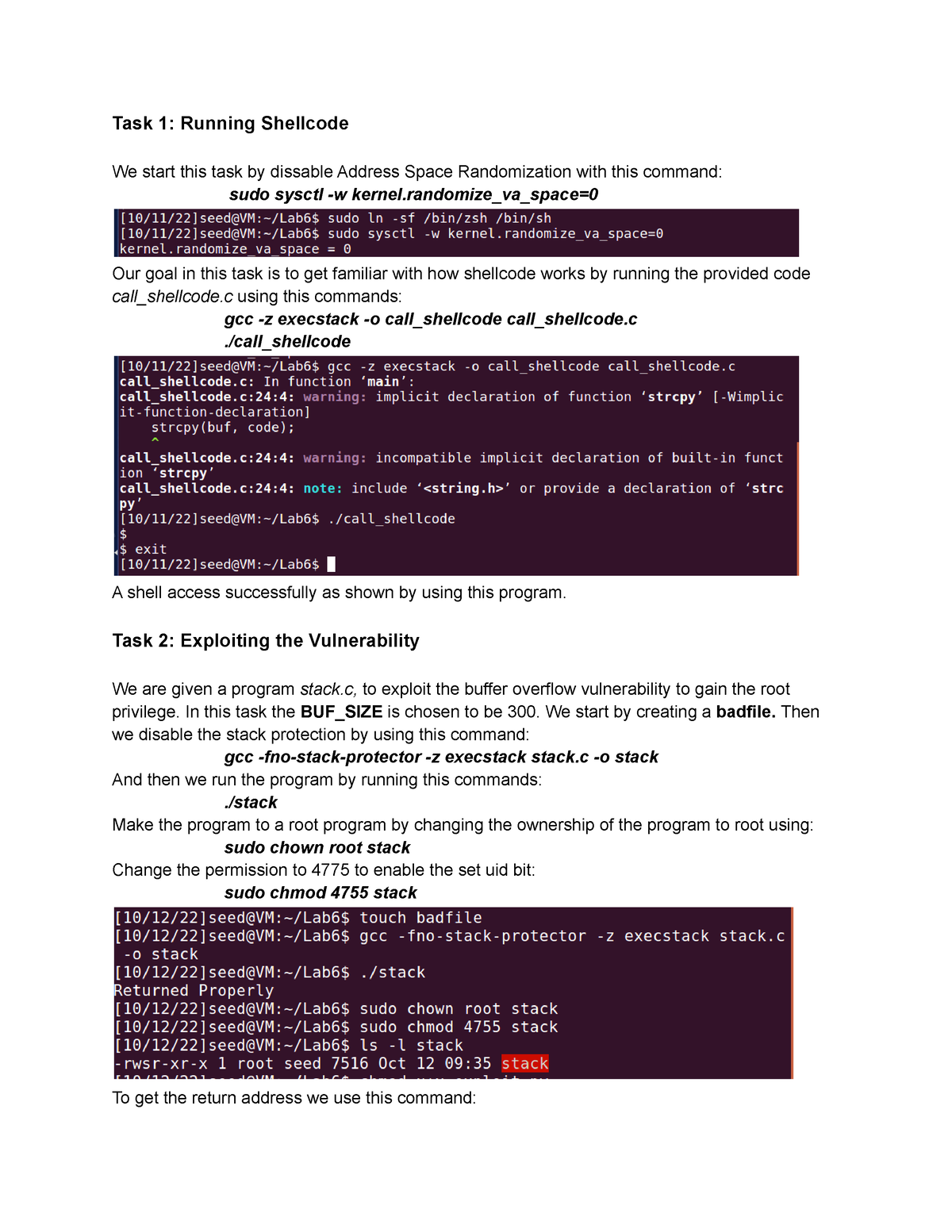
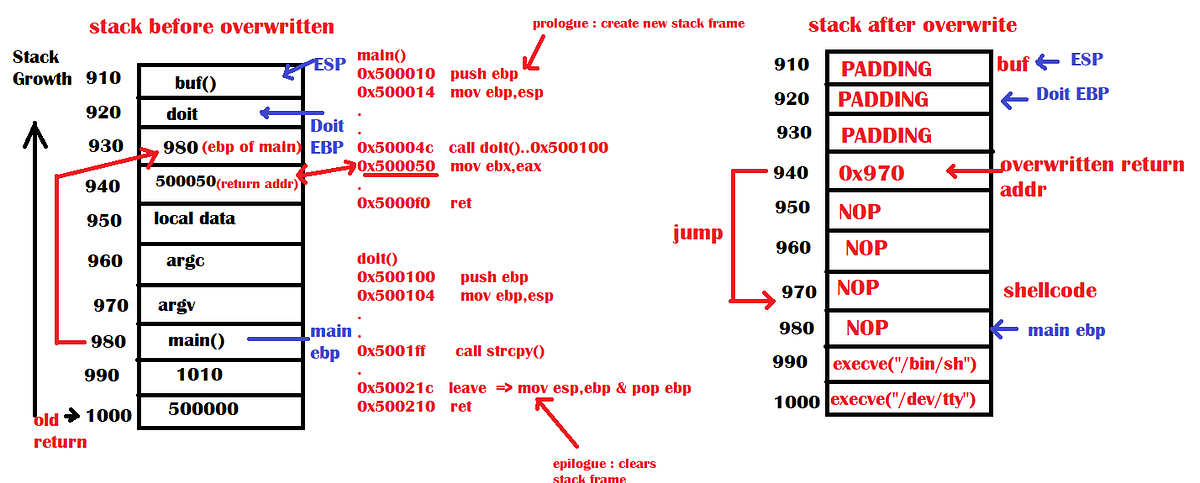
Buffer-Overflow Vulnerability Lab 6 - Task 1: Running Shellcode We start this task by dissable - Studocu