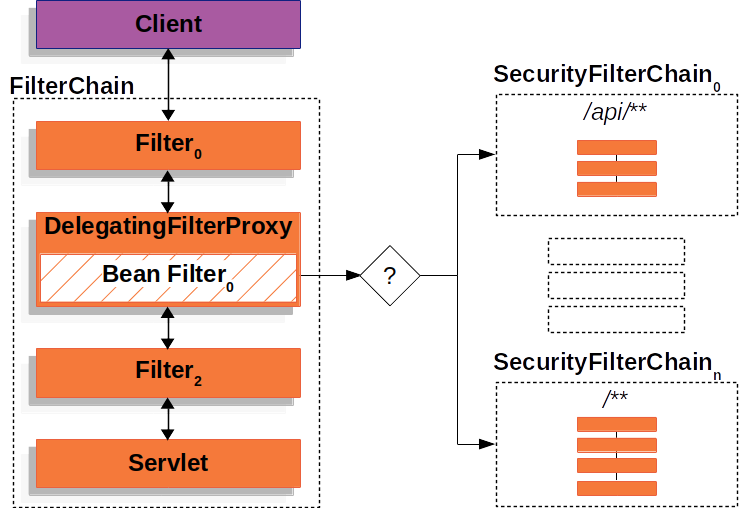
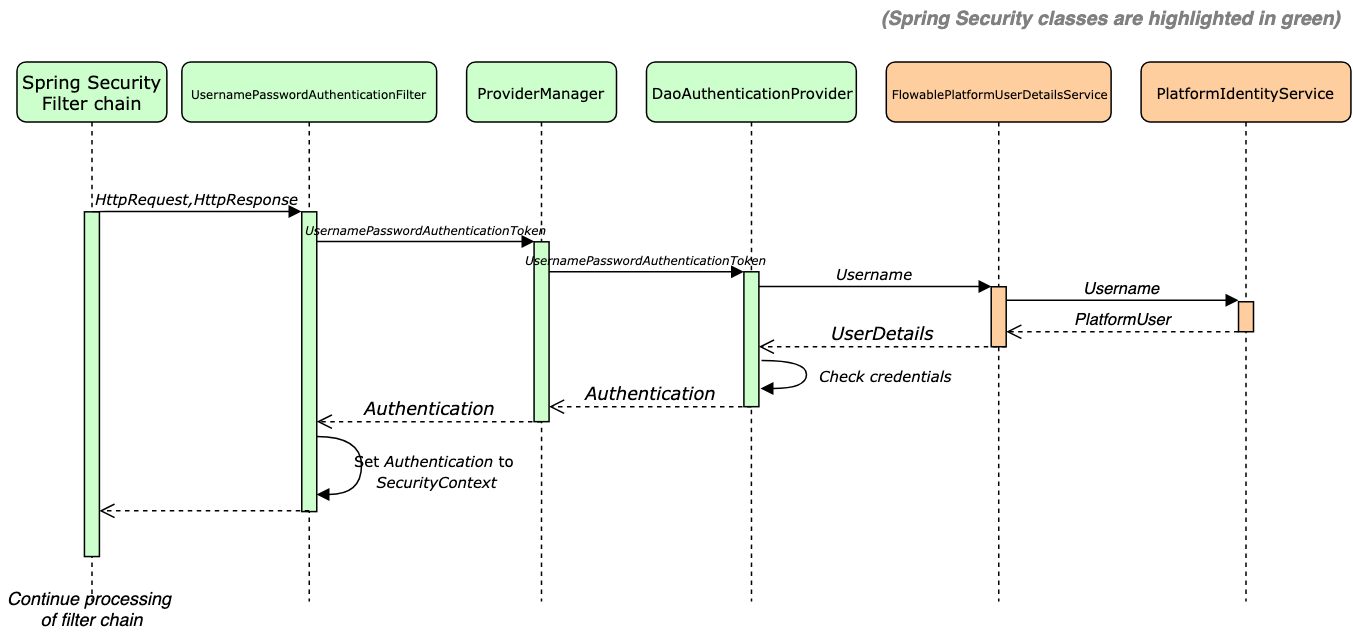
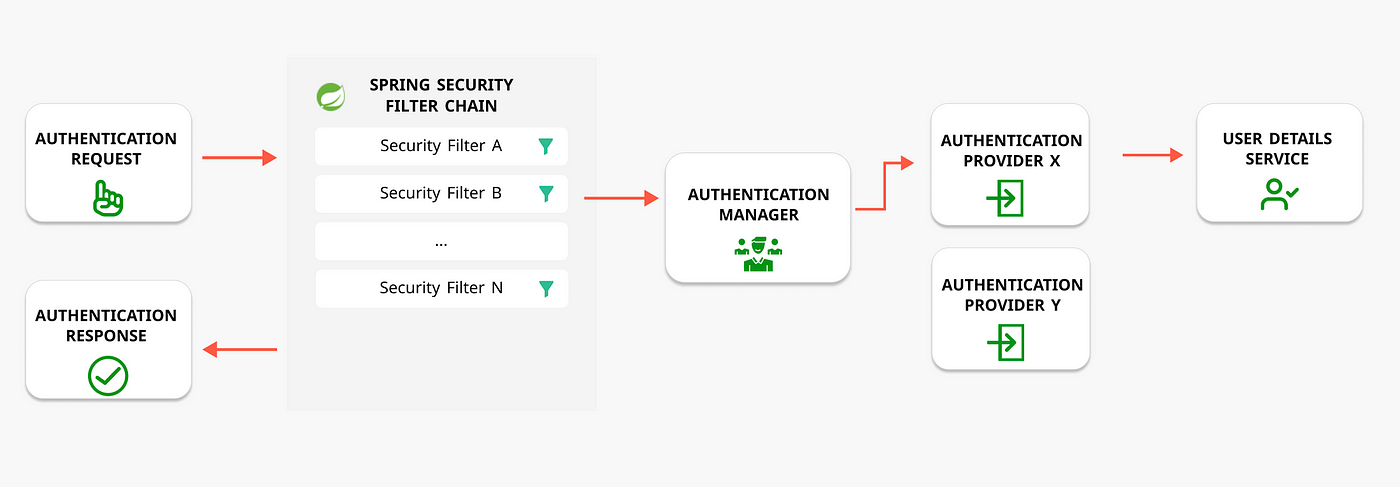
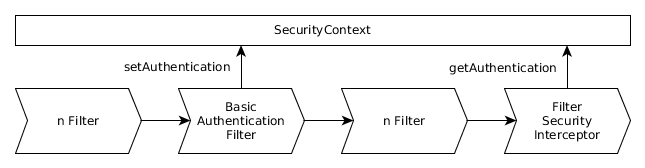
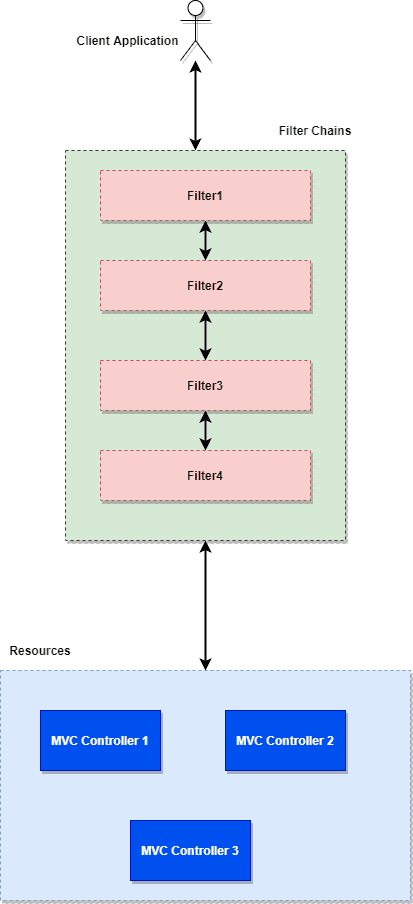
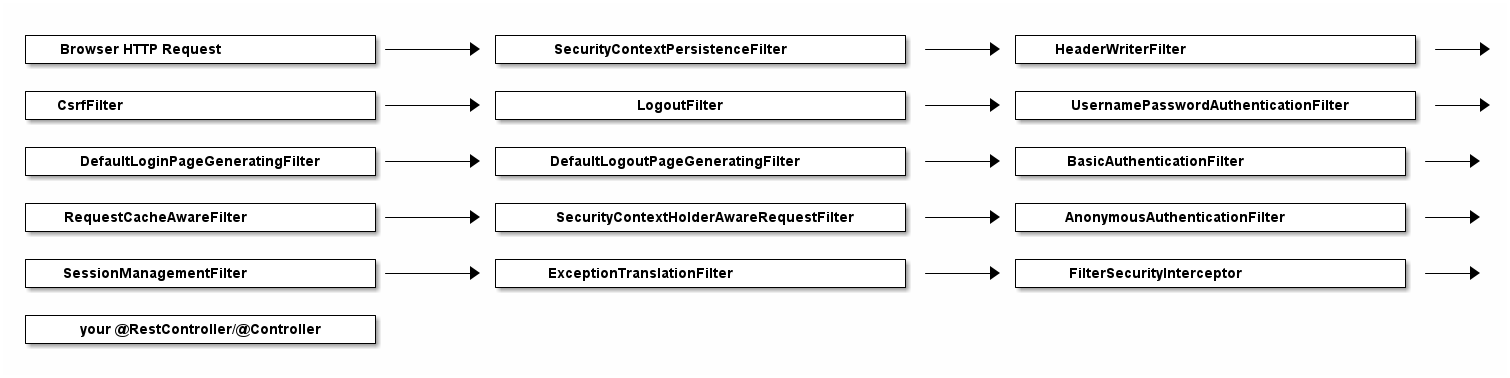
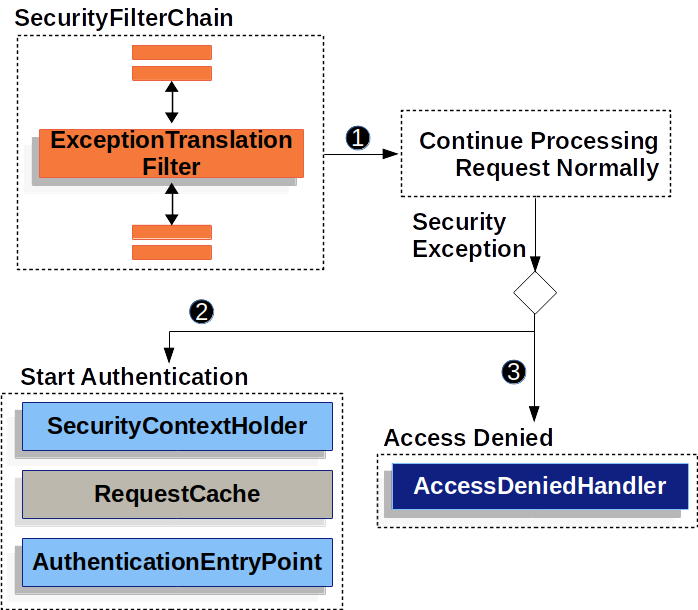
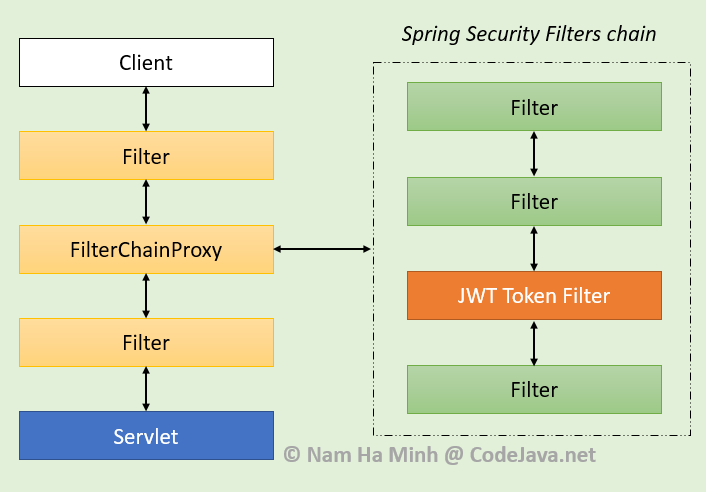
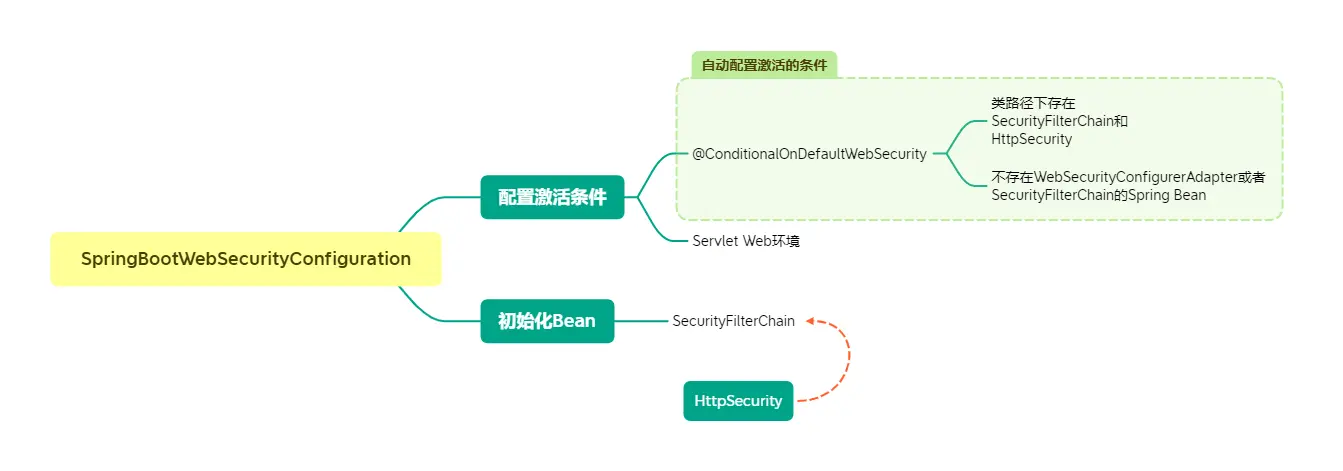
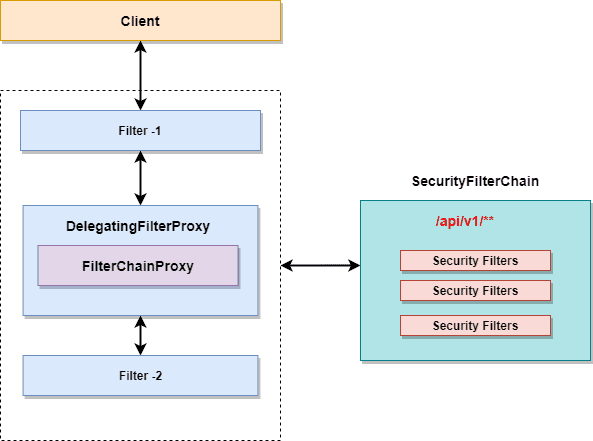
3.Spring Security Filter Chain Configuration | CRUD app with Springboot - Spring Security - Android - YouTube
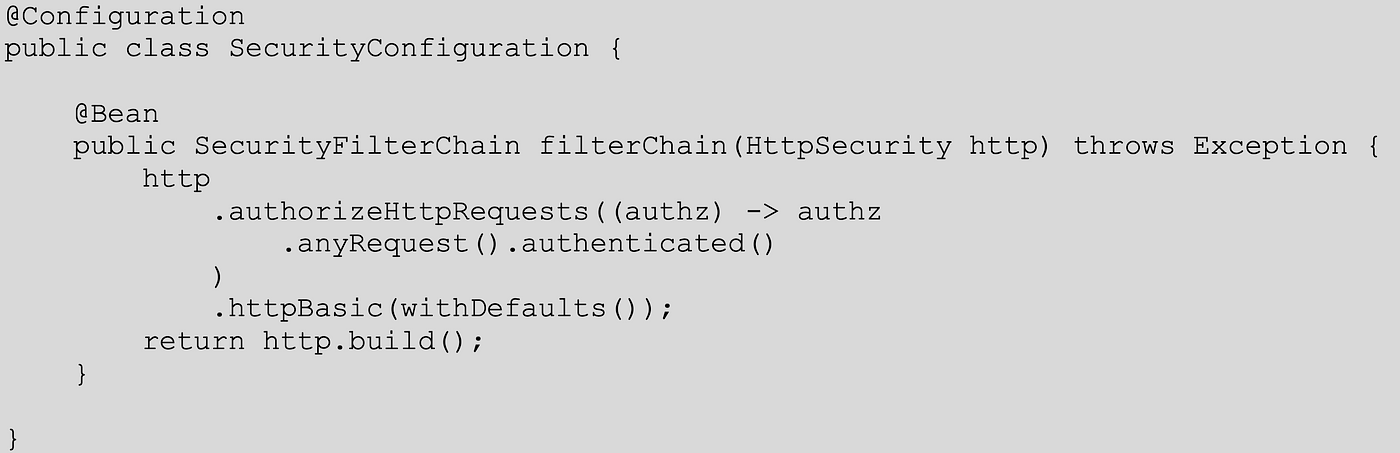
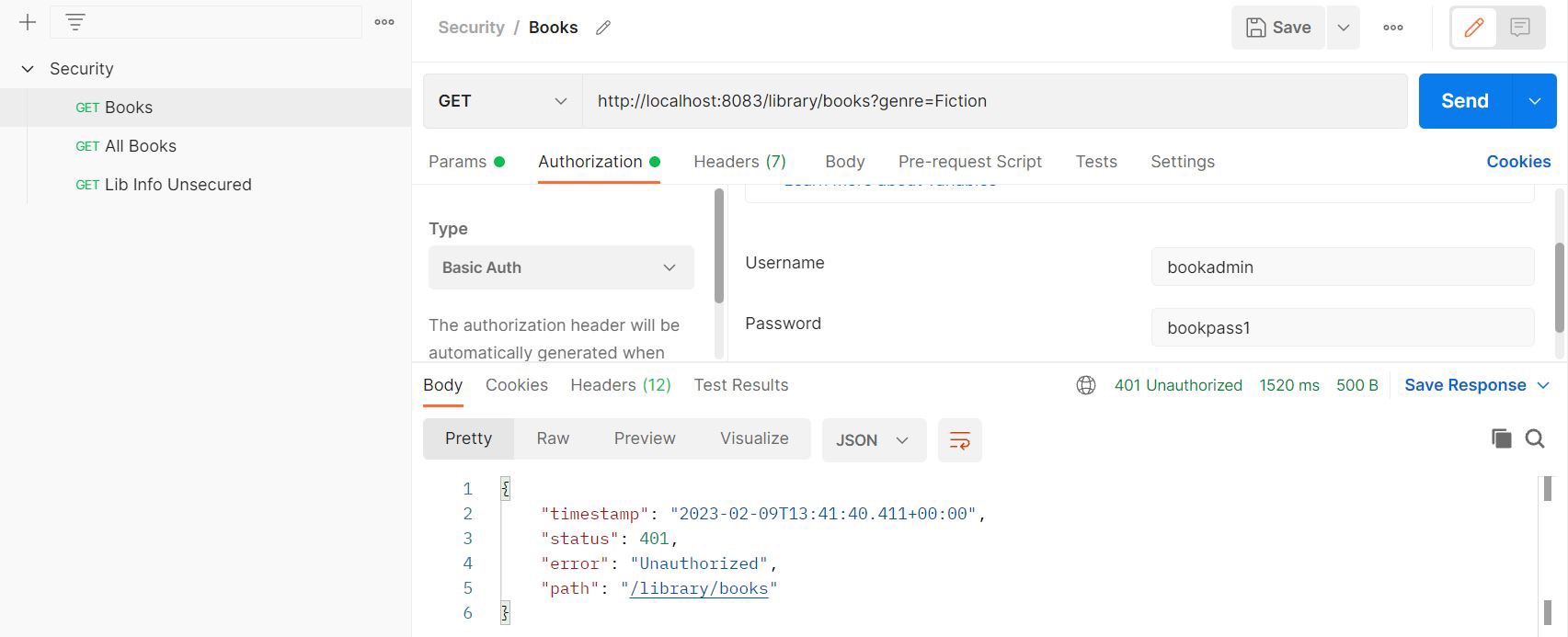
Spring Boot Security Configuration, practically explained — Part6: A deep intro to filter/token-based security | by Panos Zafeiropoulos | Dev Genius


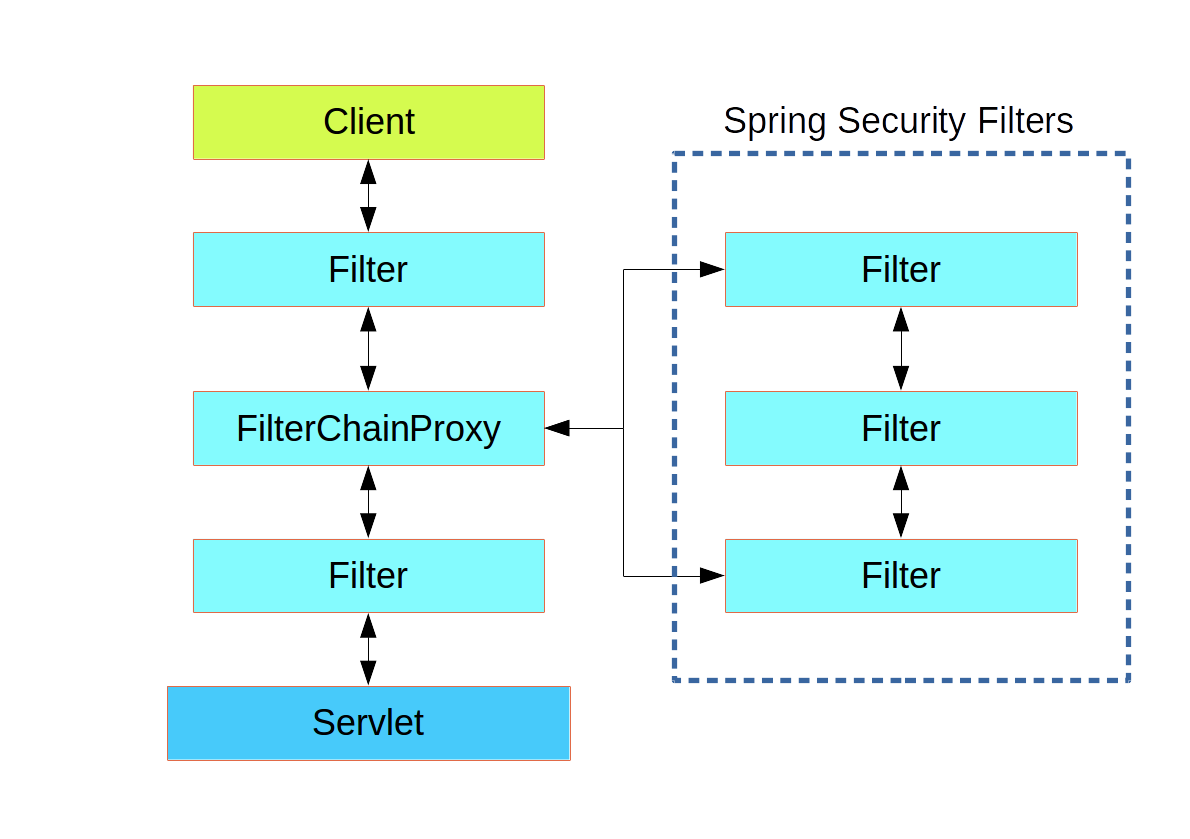
![Spring Security] 필터 Filter, SecurityFilterChain 이해하기 : 네이버 블로그 Spring Security] 필터 Filter, SecurityFilterChain 이해하기 : 네이버 블로그](https://mblogthumb-phinf.pstatic.net/MjAxNzA3MjdfMTM3/MDAxNTAxMTQzOTk2OTc5.oZfs8V6ZkiwFmZiPub2Nyr3GhkTxidzYo8iRefYgTjsg.3gsRDl0ewlc8lboDIvR_M6LJh6SnOERDCAMpMCHKlFkg.PNG.sipzirala/%EB%8B%A4%EC%9A%B4%EB%A1%9C%EB%93%9C.png?type=w420)